Network Security Tutorialspoint

Network security entails securing data against attacks while it is in transit on a network.
Network security tutorialspoint. There are popular standards for real time network security protocols such as s mime ssl tls ssh and ipsec. It covers various mechanisms deve. Threat is a possible risk that might exploit a network weakness to breach security and. Tutorialspoint published on 01 jan 2016 language.
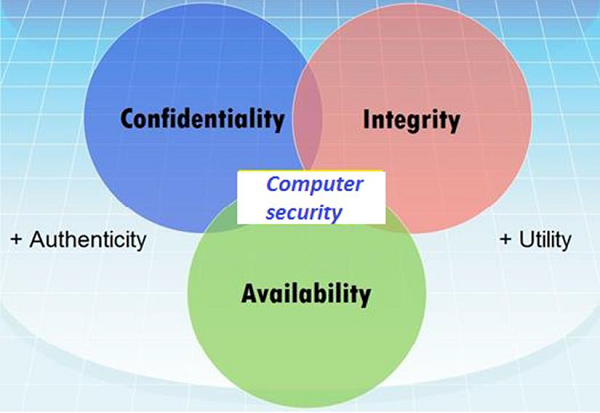
A network has two components hardware and software. To achieve this goal many real time security protocols have been designed. In the earlier chapters we discussed that many real time security. Network security 6 goals of network security as discussed in earlier sections there exists large number of vulnerabilities in the network.
Computer networks that are involved in regular transactions and communication. Another form of service denial is the disruption of an entire network wither by disabling the network or by overloading it by messages so as to degrade performance. There are popular standards for real time network security protocols such as s mime ssl tls ssh and ipsec. It is the duty of network administrators to adopt preventive measures to protect their networks from potential security threats.
Use code weekend to get extra flat 15 off. It covers various mechanisms developed to provide fundamental security services for data communication. Both these components have their own vulnerability to threats. An attacker can target the communication channel obtain the data and read the same or re insert a false message to achieve his nefarious aims.
Premium ebooks premium ebooks. Download ebook on network security tutorial network security deals with all aspects related to the protection of the sensitive information assets existing on the network. This tutorial introduces you to several types of network vulnerabilities and attacks followed by the description of. Network security deals with all aspects related to the protection of the sensitive information assets existing on the network.
This attack may have a specific target. For example an entity may suppress all messages directed to a particular destination. As mentioned earlier. It prevents normal use of communication facilities.
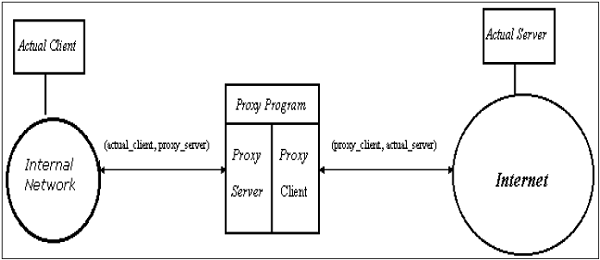
Thus during transmission data is highly vulnerable to attacks. To achieve this goal many real time security protocols have been designed. Network layer security controls have been used frequently for securing communications particularly over shared networks such as the internet because they can provide protection for many applications at once without modifying them.