Network Security Tutorial Javatpoint

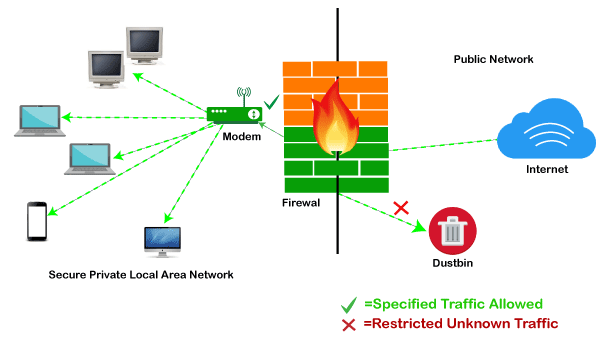
Different approaches to computer network security management have different requirements depending on the size of the computer network.
Network security tutorial javatpoint. Pgp uses a digital signature a combination of hashing and public key encryption to provide integrity authentication and non repudiation. Computer network tutorial provides basic and advanced concepts of data communication networks dcn. Cyber security technology with cybersecurity tutorial introduction cybersecurity history goals cyber attackers cyber attacks security technology threats to e commerce security policies security tools risk analysis future of cyber security etc. It covers various mechanisms deve home.
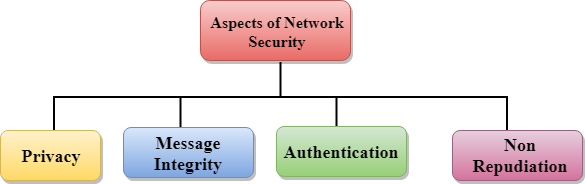
It is the duty of network administrators to adopt preventive measures to protect their networks from potential security threats. Now you are on the network security group creation page. Network security tutorial network security deals with all aspects related to the protection of the sensitive information assets existing on the network. Our computer network tutorial includes all topics of computer network such as introduction features types of computer network architecture hardware software internet intranet website lan wan etc.
Our cyber security tutorial is designed for beginners and professionals. Our computer networking tutorial is designed for beginners and professionals. Computer networks that are involved in regular transactions and communication. Our cyber security tutorial includes all topics of cyber security such as what is cyber security cyber security goals types of cyber attacks types of cyber attackers technology e commerce policies digital signature cyber security tools security risk analysis challenges etc.
Computer network security consists of measures taken by business or some organizations to monitor and prevent unauthorized access from the outside attackers. Pgp was designed to provide all four aspects of security i e privacy integrity authentication and non repudiation in the sending of email. Cyber security introduction cybersecurity is primarily about people processes and technologies working together to encompass the full range of threat reduction vulnerability reduction deterrence international engagement incident response resiliency and recovery policies and activities including computer network operations information assurance law enforcement etc. Cyber security goals with cybersecurity tutorial introduction cybersecurity history goals cyber attackers cyber attacks security technology threats to e commerce security policies security tools risk analysis future of cyber security etc.
Then select network security group and. Select the resource group fill the name select the.