Network Security Tutorial Geeksforgeeks
Effective network security defeats a variety of threats from entering or spreading on a network.
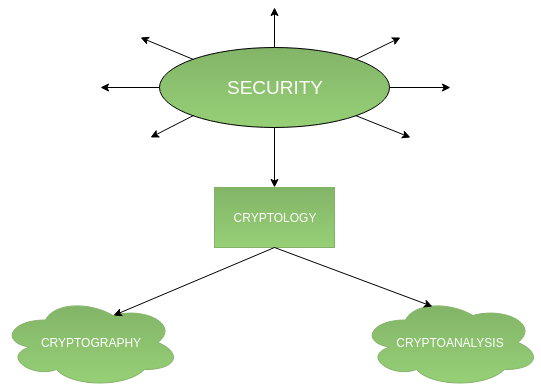
Network security tutorial geeksforgeeks. Information security is not only about securing information from unauthorized access. It also defines the encrypted decrypted and authenticated packets. Des data encryption standard or des is a symmetric key algorithm for encryption of electronic data. Cryptography is the study and practice of techniques for secure communication in the presence of third parties called adversaries.
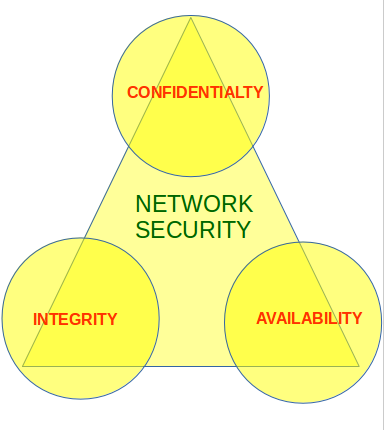
Information security is basically the practice of preventing unauthorized access use disclosure disruption modification inspection recording or destruction of information. The ip security ipsec is an internet engineering task force ietf standard suite of protocols between 2 communication points across the ip network that provide data authentication integrity and confidentiality. A computer science portal for geeks. The primary goal of network security are confidentiality integrity and availability.
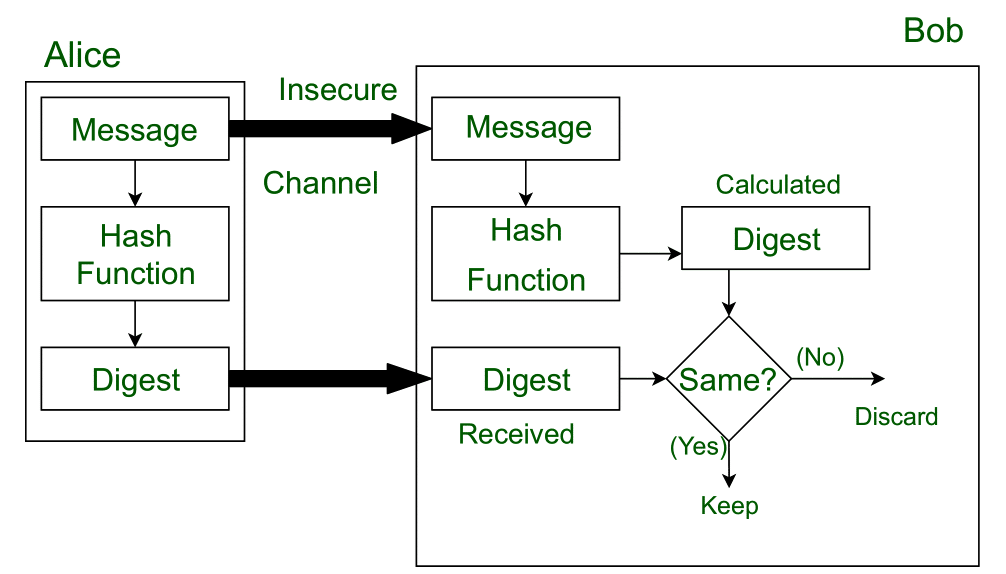
These three pillars of network security are often. Network security refers to the measures taken by any enterprise or organisation to secure its computer network and data using both hardware and software systems. It deals with developing and analyzing protocols which prevents malicious third parties from retrieving information being shared between two entities thereby following the various aspects of information security. Sha 1 secure hash algorithm 1 or sha 1 is a cryptographic hash function it produces a 160 bit 20 byte hash value message digest.
It is basically to advance our security of the system so that we can prevent unauthorized access of our system from attacker. Rsa it is an algorithm used to encrypt and decrypt messages. This aims at securing the confidentiality and accessibility of the data and network. However though the approaches of implementation are different they are complementary to each other.
Computer network security consists of measures taken by business or some organizations to monitor and prevent unauthorized access from the outside attackers. The approach to network security through access control is technically different than implementing security controls at different network layers discussed in the earlier chapters of this tutorial. Md5 message digest 5 or md5 is a widely used cryptographic hash function that. Cyber system security as the name suggest to protect our system from cyber attacks malicious attacks.
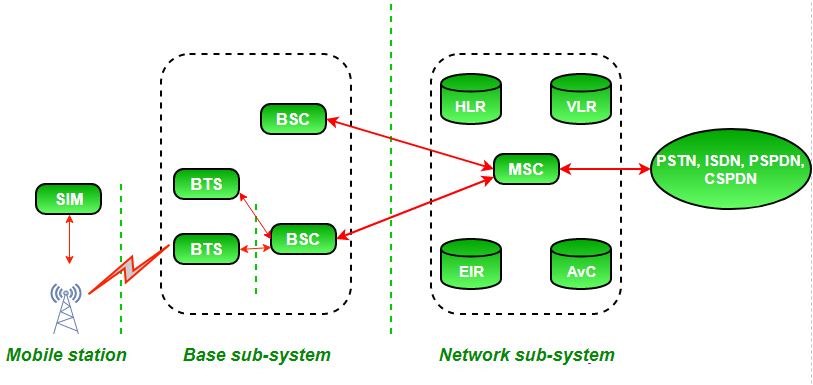
Network security entails protecting the usability reliability integrity and safety of network and data. The protocols needed for secure key exchange and key management are defined in it.