Network Security In Computer Networks Geeksforgeeks
Des data encryption standard or des is a symmetric key algorithm for encryption of electronic data.
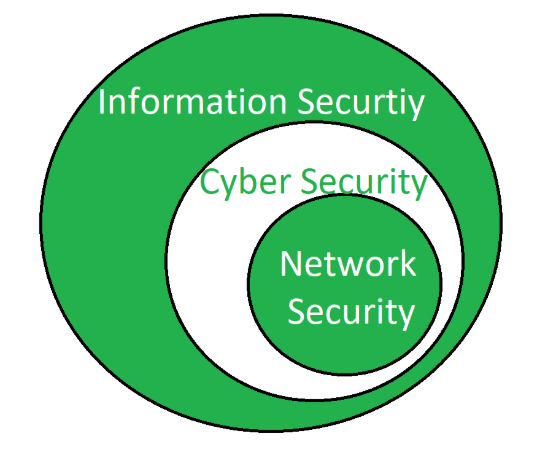
Network security in computer networks geeksforgeeks. A system is said to be secure if its resources are used and accessed as intended under all the circumstances but no system can guarantee absolute security from several of the various malicious threats and unauthorized. A computer science portal for geeks. Basics of computer networking. Last minute notes computer networks.
Sha 1 secure hash algorithm 1 or sha 1 is a cryptographic hash function it produces a 160 bit 20 byte hash value message digest. It is a process of ensuring confidentiality and integrity of the os. Practice programming coding problems categorized into difficulty level hard medium easy basic school related to computer networks topic. It contains well written well thought and well explained computer science and programming articles quizzes and practice competitive programming company interview questions.
Rsa it is an algorithm used to encrypt and decrypt messages. This aims at securing the confidentiality and accessibility of the data and network. Md5 message digest 5 or md5 is a widely used cryptographic hash function that. A computer science portal for geeks.
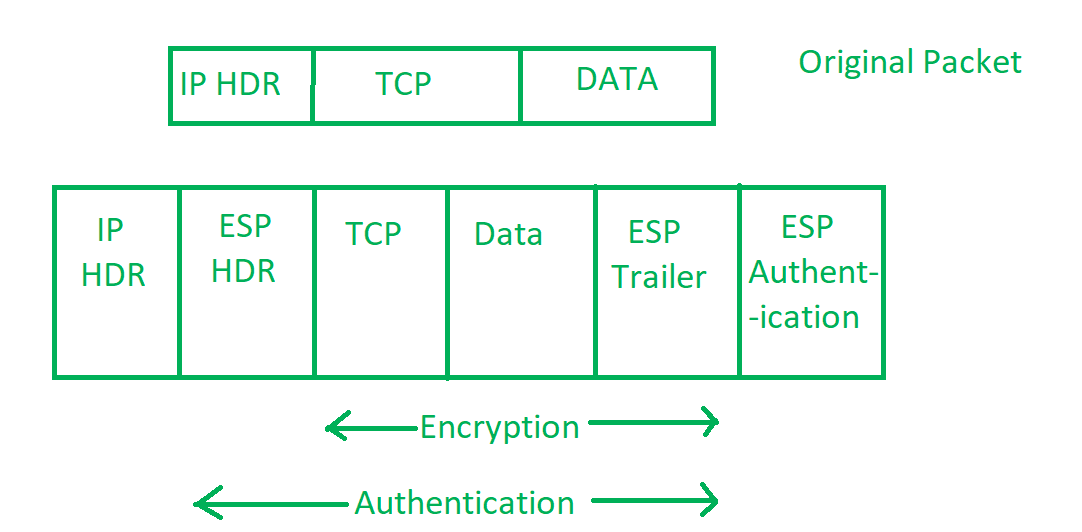
Commonly asked computer networks interview questions set 1. It contains well written well thought and well explained computer science and programming articles quizzes and practice competitive programming company interview questions. Every company or organisation that handles large amount of data has a degree of solutions against many cyber threats. It also defines the encrypted decrypted and authenticated packets.
Computer network security consists of measures taken by business or some organizations to monitor and prevent unauthorized access from the outside attackers. Network security refers to the measures taken by any enterprise or organisation to secure its computer network and data using both hardware and software systems. The ip security ipsec is an internet engineering task force ietf standard suite of protocols between 2 communication points across the ip network that provide data authentication integrity and confidentiality. Different approaches to computer network security management have different requirements depending on the size of the computer network.